The era of digital convenience has brought a wave of transnational swipe-taps that sinister threat lurks and can affect financial transactions. Clone cards are the nefarious practice of credit cards and it is raising concerns for consumers and financial institutions. It has staggering implications for global financial security.
The World where your hard-earned money can vanish in an instant because of created a replica of your credit card without your knowledge. This isn’t a fiction science. It’s a harsh reality of card cloning a sophisticated form of fraud that’s causing trouble worldwide.
In 2021, 389,737 credit card fraud reports in the United States. The numbers paint a stark picture of is growing nuisance. 80% of all credit has been compromised in circulation. The U.S. card industry is projected to lose a whopping $165.1 billion to fraud in the coming years. The financial threat and its impact are equally staggering.
Card cloning is also known as skimming. It involves the illegal replication of credit or debit card information. It enables criminals to create counterfeit cards for unauthorized transactions. According to the FBI estimate $1 billion is lost each year to skimming. This is the most prevalent form of fraud that is a threat to a significant portion of finance.
As we dig deeper into the world of clone cards, you’ll explore clone cards meaning, how this fraud works, its far-reaching consequences, and most importantly, how individuals and businesses can protect themselves from the threats in financial institutions.
What Is Card Cloning?
Credit card cloning is the electronic theft of data also known as skimming, credit card skimming, or card cloning.
Card cloning is the process of replicating the digital information stored in debit or clone credit cards to enable unauthorized charges in the victim’s name. It refers to the illegal replication of credit or debit card information.
It is a newfangled payment card equipped with radio frequency identification technology (RFID). This fraudulent practice implicates creating an exact copy of a legitimate card’s data. This enables transaction information transmission to a card reader nearby without inserting the card in a slot physically.
Criminals have developed an RFID-enabled card-cloning device that can secrete these on their bodies while walking on streets. This is how they steal information from RFID-enabled cards without a being close to card owners.
This practice involves creating an exact copy of a legitimate card’s data using an electronic device to capture and transfer data. This fraud or theft occurs at credit card terminals.
Security improvements can help to protect against these types of attacks and thefts. The use of personal identification numbers (PINs) chip cards can be helpful.
| According to A leading financial crime prevention company: “Credit card cloning fraud sometimes known as card skimming. It is a type of credit card theft in which a scammer makes a copy of a legitimate user’s credit card. This definition wraps the constitution of clone cards and underscores the unauthorized duplication of sensitive financial information. |
How Do Clone Cards Work?
Cloning, in the context of payment cards, is done through the use of skimmers. It is a technique that exploits vulnerabilities in the payment card system.
There are several ways to clone a credit card. It involves the duplication of a card’s data and its transfer onto a misleading card.
It depends on the type of technology they are built with. These counterfeit cards, then be used for fraudulent transactions.
The intricate process of credit card skimming uses a blend of technology, cunning, and criminal ingenuity. Skimmers read credit card information through PINs, and CVV data through the magnetic stripe.
These are attached to hardware such as point of sale (POS) terminals. They allow the ATMs and terminals to steal whoever uses that hardware’s information.
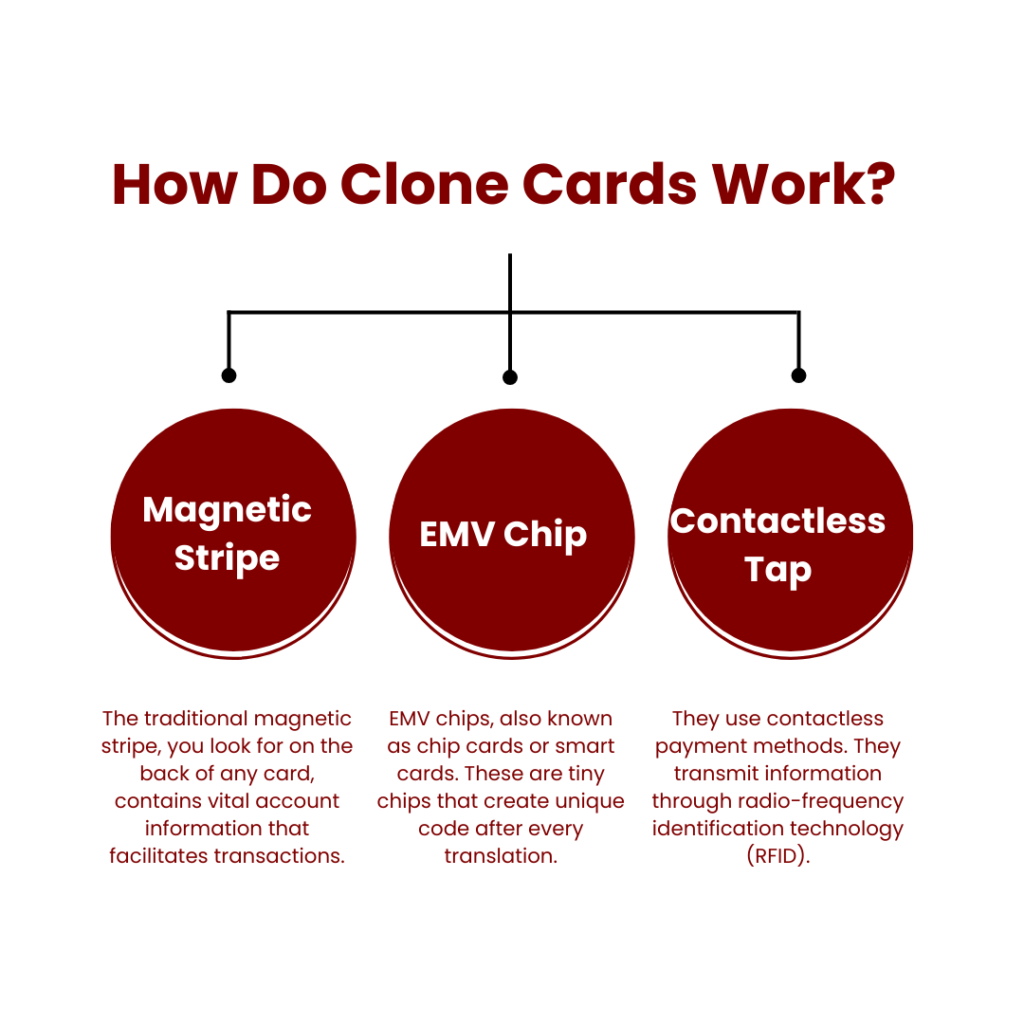
Cards can store and transmit information in three ways including
Magnetic Stripe:
The traditional magnetic stripe, you look for on the back of any card, contains vital account information that facilitates transactions. The grey strip on the back contains the magnetic swipes in parallel with the edge of about ½ inch.
This magnetic stripe is weak in security provision. These stripes use technology similar to music tapes to store information on the card.
The stored information is transmitted to a reader when the card is “swiped” at any point. Criminals use various methods to exploit vulnerability and steal the sensitive data stored on stripes.
- This method uses skimming devices and these devices change the legitimate card readers when placed over the original card readers at payment terminals.
- When the victim swipes the card skimming device steals the data captured on the magnetic stripes and allows the criminal to create a clone of the card.
- To protect magnetic stripe cloning, be vigilant when using ATMs and card terminals.
EMV Chip:
EMV chips, also known as chip cards or smart cards. These cards offer far superior cloning protection than magstripe. It is a more secure alternative. These chips protect each transaction with a secure code that is useless if replicated.
These are tiny chips that create unique code after every translation. This is a more secure and challenging way for fraudsters to create counterfeit cards. On the front side of most newer cards is a small rectangular metallic insert with short edges.
- There are less impassable EMV chips that are not immune to the cunning tactics of fraud.
- EMV microchip uses advanced technologies for the secure transmission of data information.
- Unfortunately, criminals have developed technology to bypass these security measures through card skimming.
- It is more reliable but you still need to stay cautious about your cards before using them.
Contactless Tap:
The recent cards introduced in the market today are equipped with a third way of storing and transmitting information.
They use contactless payment methods. They transmit information through radio-frequency identification technology (RFID).
This technology uses wireless to transmit payment information. This technology doesn’t need physical contact with card and payment terminal. That’s why it is referred to as “smart cards” or “tap to pay” transactions.
- contactless payment offers a seamless and efficient experience.
- Contactless payments offer increased protection against card cloning.
- criminals have developed ways of intercepting the communication between cards and payment terminals.
- Staying informed about methods employed by criminals and vulnerabilities and adopting best practices to safeguard fraud and threats is essential.
Examples Of Credit Card Cloning Fraud:
There are different ways to steal information that is necessary to make a clone card. The fraudulent can look into someone’s shoulder to know the PIN of the card.
There are other ways and tricks of knowing someone’s information. Installing a fake keypad on an ATM or point of sale device to copy the information of the card can be one of the credit card cloning fraud examples.
The detailed examples include
Card Skimming:
Criminals create skimming devices and attach them to the point-of-sale terminals. These terminals include gas pumps, ATMs, and merchant card readers.
The skimming devices steal the information and store the data for fraudsters who use this information for card cloning.
Atm Skimming:
Fraudsters use skimming devices at ATMS and capture the information of bank cards. It is an illegal process to access someone’s bank account details.
Skimmers place the card reader on top of the original card reader with a similar size, color, and texture difficult to identify.
They place the camera near the ATM and they can view the keypad and also the keys they press and steal the PINs and use it for illegal activities.
Statistics On Credit Card Cloning
| Statistics | Value |
| Americans experienced credit card fraud in 2024. | 62 million |
| Unauthorized purchases in the US (2024) | $6.2 billion |
| Increase in e-commerce credit card fraud in the US (last 3 years) | 140% |
| Percentage of global credit card fraud in the US. | 46% |
| 2,000 reported cases of credit card fraud in Singapore in 2019. | Estimated loss of SGD 6.6 million |
| Philippine National Police-Anti-Cybercrime Group recorded cases in 2020. | 800 cases |
What Are Ways To Prevent Card Cloning?
It is important to adopt precocious measures to protect yourself from card cloning and financial fraud.
This is the era of digital tech, where online fraud and threats are common issues for all. online transactions and contactless payments are common.
It is important to safeguard your information against any illegal activity. There are different vigilant ways of proactive measures that can reduce the risk of fraudulent activities.
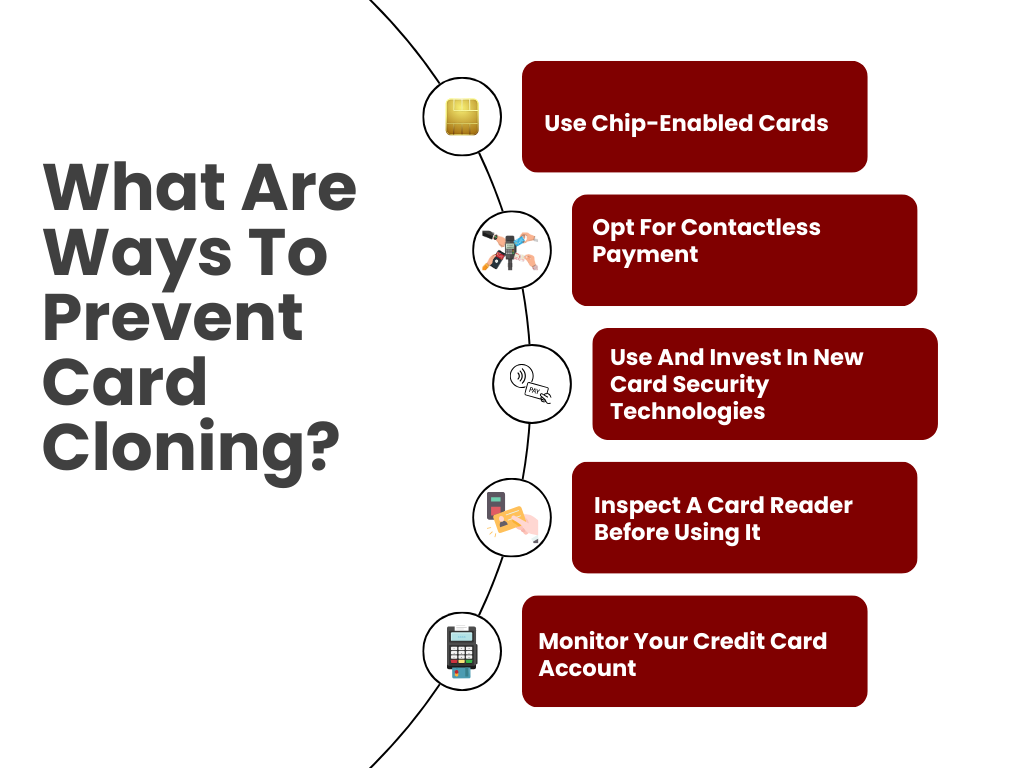
These ways can include:
Use Chip-Enabled Cards:
Credit cards with chip-enabled technologies are safer to protect your card against card cloning. These cards use EVM technology instead of magnetic stripe cards.
Opt For Contactless Payment:
Consider contactless payment methods. They use mobile wallets or cards with NFC technology. These methods are more secure than traditional transaction methods. Contactless payments, encrypting your card information. Fraudsters can’t intercept and misuse your data.
Use And Invest In New Card Security Technologies:
EMV chips and the RFID newest technologies make it harder for criminals to clone cards. Europay, Mastercard, and Visa (EVM) chips are the biggest advancements in the fight against card cloning.
They use payment to use encrypted information and it is exceptionally difficult for criminals to clone cards.
Inspect A Card Reader Before Using It:
Card inspection is important before making any translation. Inspect your card reader before you insert your card into a payment terminal. Don’t do any activity if something looks suspicious.
Some skimming devices can be bulky. Others just look a little klutzy.
Monitor Your Credit Card Account:
Review your credit card statements for daily transactions. Report it to your bank immediately if you notice unusual activity.
keeping track of your expenses and transactions can help you spot any discrepancies and take swift action to address them.
Sign Up For Alerts:
Financial institutions offer transaction alerts via SMS or email. Being part of these services you can receive real-time notifications about activity on your credit card.
These alerts help you stay informed about your account activity and unusual or unauthorized transactions.
Final Thoughts:
Clone card scams are an increasing threat in the digital financial landscape. It’s important to know how it works to implement security measures. Any individual and financial institution can reduce the risk with the precautionary measures discussed above.
Head of AI at a fact-checking organization, Andrew Dudfield stated, “The UK government’s decision risks undercutting its hard-won credibility as a world leader for safe, ethical and trustworthy AI innovation”. This represents the importance of staying ahead and vigilant for evolving financial threats.
FAQs:
What Are Clone Cards?
Credit card cloning is the electronic theft of data also known as skimming, credit card skimming, or card cloning.
How To Clone Cards?
Card cloning occurs when your credit card data has been stolen. Once a skimmer captures your card’s information, it can be copied onto a blank card or overwritten onto another stolen card.
How Do Clone Cards Work?
Clone cards work illegally. It copies the digital information from a legitimate credit card onto a counterfeit card. Is s how criminals make unauthorized transactions
What Happens If Your Card Has Been Cloned?
It can result in the loss of clone cards with money and can disrupt your transitional process.
Is It Legal To Clone Your Card?
No, it’s not legal to clone your own credit or debit card. It is considered fraudulent and violates banking regulations and card issuer agreements.
People are also Reading:












+ There are no comments
Add yours