In the Continuously transforming cybersecurity sphere, SOC compliance has become a standard for organizations to handle sensitive customer data.
The importance of SOC 2 is continuously growing as we enter 2025. The attestation of its continuous expansion is highlighted with compelling statistics.
The adaptation of SOC 2 Compliance Increased by 40% in 2024, and this underlines its recognition in the business world.
60% of the companies are likely to work with new startups that have accomplished SOC 2 Compliance.
Capitalists prefer investing in companies with SOC Compliance at the rate of 70%. This is how it impacts funding opportunities.
Organizations with SOC 2-type Compliance have reported an improvement of 72% in data security and the customer satisfaction rate increased by 68%.
These statistics highlight the Constantly shifting realm of SOC 2 compliance. This is a digital era where the need for SOC 2 compliance is fundamental. The average cost of SOC2 type 1 preparation and certification ranges from $91,000 for small companies.
For medium-sized enterprises, it ranges to $186,000. Businesses are investing in their security posture. With increased cyber threats data protection is critical. SOC2 compliance stands out in the digital age of security.
Organizations that deal with customer data must exhibit their devotion to protecting their data. SOC 2 compliance is the recognized framework for the protection of data.
This blog will explain the SOC 2 compliance definition, its benefits, the SOC 2 compliance checklist, and how to fulfill SOC 2 Compliance certification.
What Is Soc 2 Compliance?
SOC 2 compliance is a voluntary framework designed by the American Institute of CPAs (AICPA). It ensures that service organizations securely manage and protect customer data.
It safeguards the interests of an organization and the privacy of its clients. It is part of the SOC 1 and SOC 2 compliance standards. SOC stands for “System and Organization Controls”.
The number 2 represents the set of focused criteria. It focuses on five trust service principles.
The SOC 2 compliance meaning includes the controls implemented in your organization to protect the sensitive information of customers. Unlike SOC 1 compliance, it focuses on financial reporting based on technology and cloud-based computing services.
Companies need SOC2 certification to provide a comprehensive SOC2 Compliance report to their customers. This proves their commitment to data security.
The Five Trust Service Principles
SOC 2 complaint is based on the criteria of Five Trust Services (TSC). it is considered the foundation of a compliance framework.
- Security: The protection of the system against unauthorized access including physical and logical.
- Availability: Availability of systems for different operations to use as committed or agreed.
- Processing Integrity: Complete Processing of the system with validity, accuracy, timely, and authority.
- Confidentiality: Confidential information is protected as confidential and protected as committed or agreed.
- Privacy: Keeping the collected Personal information retained, disclosed, and disposed of with commitments and privacy notice entity. It is the criteria set by Generally Accepted Privacy Principles (GAPP)
| 📌Point to note Security criterion is mandatory for all SOC 2 audits. Organizations can set and choose additional criteria based on business or client needs and requirements. |
Why Is Soc 2 Compliance Important?
SOC 2 compliance accomplishment offers various benefits to organizations and businesses including
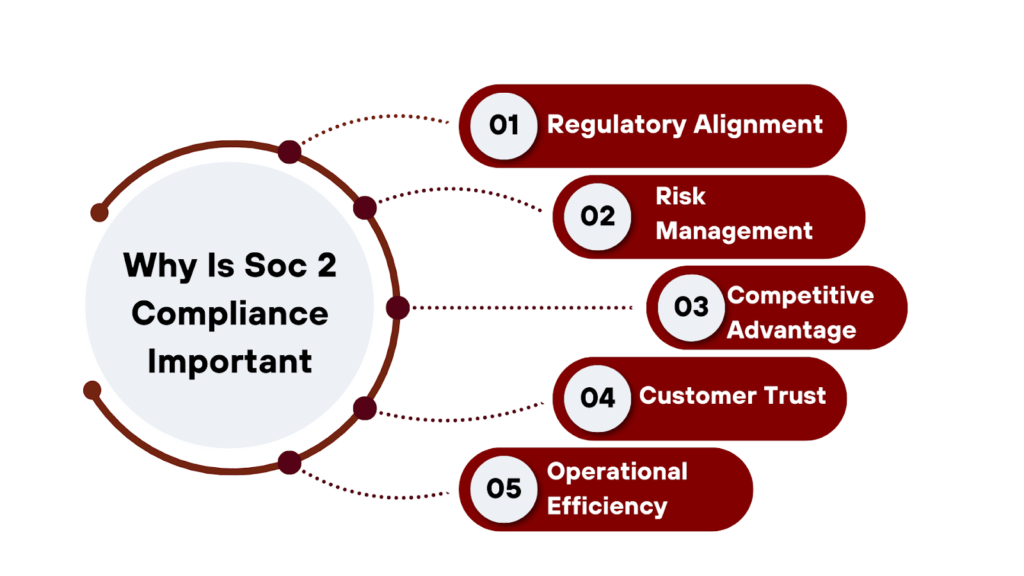
Customer Trust
Customers trust businesses that can demonstrate SOC 2 security compliance. It offers a commitment to data security and privacy to customers and clients.
Competitive Advantage
companies that are SOC2 certified can be a differentiator in industries. They stand out where data protection is crucial and a priority.
Risk Management
SOC 2 controls limit data breaches and cyberattacks. It helps in the identification of security vulnerabilities and addressing strategies to mitigate risk.
Regulatory Alignment
SOC 2 compliance requirements align with various data protection regulations. It easing overall compliance efforts and other regulations including GDPR compliance and HIPAA Compliance.
Operational Efficiency
It improves internal processes and controls. It handles data and operations stability.
| 📌SOC 2 compliance for startups can be a game changer for startup businesses. It helps in attracting other enterprise clients who demand Secure data management standards. |
Types Of Soc 2 Reports
There are two types of SOC 2 compliance reports including
- SOC 2 Type 1: This report evaluates the design of security processes at a certain point in time.
- SOC 2 Type 2: This report evaluates how effective the controls are over some time (usually 6-12 months)
SOC 2 Type 1 vs. Type 2 Compliance:
| Specific Aspects | SOC 2 Type 1 Compliance | SOC 2 Type 2 Compliance |
| Focus | The focus is on designed controls at a particular point in time. | The effectiveness of control is over a period (from 6-12 months). |
| Timeframe | It provides Point-in-time assessment. | It is an Ongoing assessment over a defined period. |
| Complexity | It is less complex and faster to accomplish. | It is more detailed and time-consuming. |
| Use Case | This is ideal for organizations new to SOC 2 compliance. | This is reliable for organizations with mature controls. |
| 📌SOC 2 Type 1 compliance is a comprehensive version of the starting point, SOC 2 Type 2 compliance is seen as highly valuable because it displays sustained complaints to the framework. |
How To Get Soc 2 Compliance?
SOC 2 compliance audit can be a complicated process. It includes careful planning and execution. A comprehensive checklist can help you to get started, it includes
Define Clear Objectives
It is very important to define objectives. This gives an idea of why your organization needs SOC 2 compliance and what it wants to achieve.
Choose An Auditor
An independent and qualified auditor can help you audit your organizational processes.
Document Report Type
Select between SOC Type 2 compliance and Type 1 based on your need and preparation to opt.
Define Audit Scope
Recognize systems, applications, and data that will be included in the audit.
Perform A Gap Assessment
Conduct current controls assessment against SOC 2 requirements to know the space for improvements.
Implement Document Controls
Set and implement the security controls. Implement the documented policies and procedures in your organization. SOC 2 compliance software like Vanta SOC 2 can automate the control and monitoring process.
Conduct Internal Audit
A thorough assessment is essential before presenting to officials.
Remediate Issues
Identify and address the weaknesses during an internal audit.
Explain External Audit
Collect and gather all the documentation and evidence for the auditor. Work with an external auditor to complete the SOC 2 audit process
Review And Finalize Reports
Review the detailed draft report and then finalize it with the auditor.
Continuous Ongoing Compliance
To keep the activities on track continuously monitor and improve controls.
| 📌SOC 2 cloud compliance is important for organizations using SOC 2 cloud compliance. Different platforms including AWS SOC 2 compliance can provide and ensure the cloud infrastructure needs and standards. |
What Are The Components Of Soc 2 Compliance
The organization must implement and maintain controls across different areas to achieve SOC 2 compliance. The major components of Components of SOC 2 Compliance include:
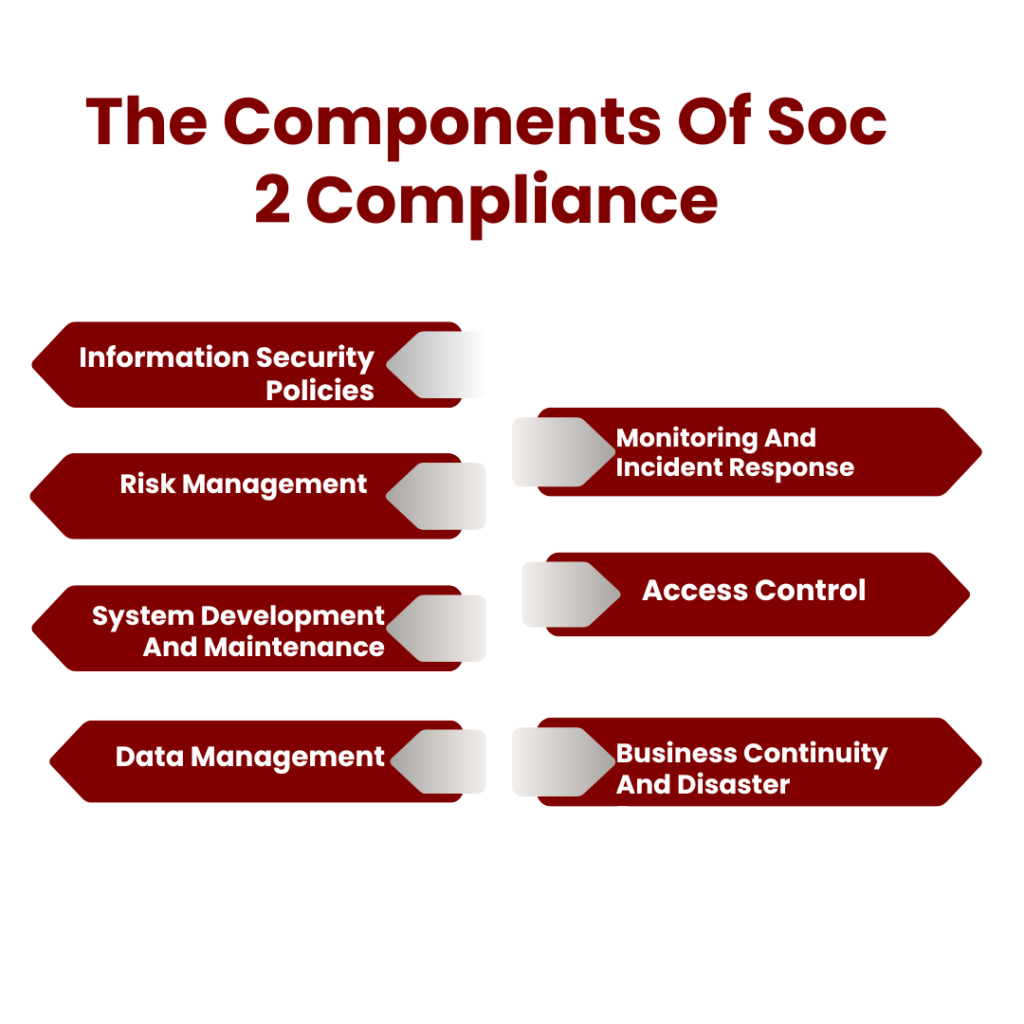
Information Security Policies
- Organize a piece of detailed information on a security control program
- Advise, maintain, and convey policies and procedures
- Review and update organization structure frequently
Risk Management
- Perform risk assessment of in-scope environment
- Conduct documented risk mitigation strategies
- Direct vendor risk management program
Access Control
- Apply strong logical and physical access controls
- Check and review the updated access permissions
- Use multi-factor authentication
System Development And Maintenance
- Carry out change management procedures where applicable
- Organize secure coding practices
- Patch the system regularly
Data Management
- Manage and maintain up-to-date information
- Carry out proper data retention and disposal practices
- Put in place the data classification and handling procedures
Monitoring And Incident Response
- Set the logging and monitoring solutions
- Test and incident the response plan
- Scans the regular penetration tests
Business Continuity And Disaster Recovery
- Test the continuity plans
- Implement the recovery procedures
- Verify the redundancy and critical system of data
Soc 2 Compliance Framework Vs. Other Compliance Frameworks
SOC 2 compliance and ISO 2700 are widely recognized for data security. It serves different purposes. The essentials to understanding it with other compliance frameworks include:
| Aspect | SOC 2 Compliance | ISO 27001 |
| Scope | Its Focus is on data security for service organizations. | It has a broader framework for information security management. |
| Certification | It Results in a SOC 2 compliance report. | It Results in an ISO 27001 certification. |
| Geographic Focus | It is primarily used in the U.S | It’s typically recognized Internationally |
| Flexibility | It is more prescriptive in its requirements. | It is personalized to specific trust principles. |
Who Needs Soc 2 Compliance?
Companies and organizations handling sensitive customer data need SOC 2 compliance. The sector includes technology and cloud services. This includes
- SaaS companies/Saas Providers
- Data centers (data center compliance)
- Cloud service providers (AWS SOC 2 compliance)/Cloud computing
- Startups looking to scale (SOC 2 compliance for startups)
- Financial institutions
- Healthcare organizations
Challenges And Best Practices
It is challenging for smaller organizations to achieve SOC 2 Compliance. SOC 2 compliance solutions and best practices can help the organization maintain it. The challenges include:
- Limited resources including time, budget, and personnel
- Complex Requirements
- Maintenance and continuous monitoring
- Keeping up with the transformative nature of regulations
Following are the best practices to keep up with these challenges.
Act Early
Start your preparation to deal with SOC 2 compliance with your target audit date.
Engage Stakeholders
Key personnel across various organizations can help the organization with the compliance process.
Support Automation
soc 2 compliance automation software can streamline the process well with fewer or no errors.
Keep Up With Continuous Improvement
Treat the compliance process as an ongoing activity. It’s not a one-time event. There is always room for improvement.
Educate And Train Employees
Conduct regular training and education seminars for employees to understand and maintain the best compliance practices.
Document Everything
clear and up-to-date SOC 2 compliance documentation with policies and procedures will maintain transparency and improvement.
Learn From Audits
soc2 compliance software can help to audit and improve the setbacks.
Benefits of SOC 2 Compliance
The benefits of SOC 2 compliance are beyond meeting regulatory requirements. They help gain including
- Being compliant with SOC2 certification builds trust with customers and data security controls.
- SOC 2 controls lead to efficient operational processes.
- It provides a competitive edge to organizations that are SOC 2 compliant.
- It reduces the risk and limits the data breaches.
Final Thoughts
In an era of data breaches and privacy concerns, Achieving SOC 2 compliance is critical. Organizations that value data security and customer trust can continuously improve their security posture.
SOC 2 compliance checklist compliance software, and understanding the differences between SOC 2 Type 1 vs. Type 2 compliance can streamline your business growth.
security practices and data protection processes can build client, partner, and stakeholder trust. Foster a continuous culture of security and it will serve your organization well in the future.
FAQs
What Does Soc 2 Compliance Mean?
SOC 2 compliance is a voluntary framework designed by the American Institute of CPAs (AICPA).
It ensures that service organizations securely manage and protect customer data. It safeguards the interests of an organization and the privacy of its clients.
What Is The Soc 2 Compliance Checklist?
Compliance check include
- Define clear Objectives
- Choose an Auditor
- Document Report Type
- Define Audit Scope
- Perform a Gap Assessment
- Implement Document Controls
- Conduct Internal Audit
- Review and Finalize Reports
- Continuous Ongoing Compliance
What Are The 5 Principles Of Soc 2?
Five principles of SOC 2 include
- Security
- Processing Integrity
- Availability
- Confidentiality
- Privacy
Is Iso 27001 The Same As Soc 2?
No, SOC 2 focuses on data security for service organizations while ISO 27001 broader framework for information security management.
Who Needs Soc 2 Compliance?
Organizations that need SOC 2 compliance include
- SaaS companies/Saas Providers
- Data centers (data center compliance)
- Cloud service providers (AWS SOC 2 compliance)/Cloud computing
- Startups looking to scale (SOC 2 compliance for startups)
- Financial institutions
- Healthcare organizations
How To Get Soc 2 Compliance?
Achieve SOC 2 compliance includes several steps including
- Define Scope
- Select Trust Principles
- Implement Controls
- Educate Your Team
- Conduct Audits
- Address Findings
- Accomplish Certification












+ There are no comments
Add yours